Ryuk. Once a name unique to a fictional character from a popular Japanese manga or manga series, it has now become a name that appears on the roster of some of the most malicious ransomware to grace the wild web.
Ryuk ransomware has been around for just 15 months, so achieving such notoriety is quite a feat for an incredibly young stock. Unless the attackers behind that campaign demand a halt (remember GandCrab?) or law enforcement permanently strangles them, we can only expect the Ryuk threat to continue to loom over organizations. .
First discovered in mid-August 2018, Ryuk quickly gained attention after disrupting operations at all Tribune Publishing newspaper offices during the Christmas holidays that year. Initially thought to be a server outage, it quickly became clear to those affected that it was actually a malware attack. It was eventually isolated. However, when the technical team took the server back, security patches were not applied, allowing Ryuk to reinfect and spread to connected systems within the network.
Big game hunting with Ryuk ransomware
Prior to the holiday attack on Tribune Publishing, Ryuk was observed targeting various corporate organizations around the world, demanding ransom payments ranging from 15 to 50 Bitcoins (BTC). This equates to between $97,000 and $320,000 at the time of valuation.
This method of targeting only large organizations with significant assets, which almost always guarantees a high ROI for criminals, is called “big game hunting.” Such targeted attacks are difficult to pull off, as they also involve customizing the campaign to best suit the target, thereby increasing its likelihood of effectiveness. This requires much more work than a simple “spray-and-pray” approach, which may capture a large number of targets but may not provide much benefit.
For threat actors engaged in big game hunting, malicious campaigns are launched in stages. For example, they may start with a phishing attack to collect key credentials, or they may drop malware within an organization's network and perform extensive mapping to identify critical assets to target. They could then deploy the second and third stages of a large-scale espionage, extortion, and ultimately ransom attack.
Currently, Ryuk ransomware is rated as the most expensive ransomware of its kind. A report from Coveware, the first incident response company specializing in ransomware, claims that Ryuk's ransom is highly negotiable, even though its asking price is 10 times the average. The variety of ways adversaries execute ransom payments suggests there may be multiple criminal groups accessing and operating Ryuk ransomware.
The person behind Ryuk
Accurately identifying the origin of an attack or malware is critical as it reveals a lot about not only the payload itself, but also the threat actor behind the attack campaign. Although the name “Ryuk” has clear ties to Japan, it is not a factor to consider when trying to pinpoint the creator of this ransomware. After all, it's common for cybercriminals to use handles based on their favorite anime or manga characters. These days, malware types are more than just their names.
Rather, similarities in code base, structure, attack vectors, and language may indicate a relationship between a criminal group and its malware family. Security researchers at Check Point discovered the link between Ryuk ransomware and Hermes ransomware early on due to similarities in code and structure, and the link continues to this day. This has led many to believe that Ryuk may also have ties to Lazarus Group, the same North Korean APT group that operated Hermes ransomware in the past.
Recommended reading: Hermes ransomware distributed to Koreans via recent Flash zero-day
However, code similarity alone is not sufficient evidence to support a link between Ryuk and North Korea. Hermes is a ransomware kit that frequently circulates in the underground market, allowing other cybercriminals to use it in their attack campaigns. Additionally, separate research by cybersecurity experts from CrowdStrike, FireEye, Kryptos Logic, and McAfee suggests that the gang behind Ryuk may actually be from Russia and not necessarily backed by a nation-state. It is shown that there is.
As of this writing, Ryuk ransomware can be traced (with high confidence, according to some in the cybersecurity community) to two criminal organizations: Wizard Spider and CryptoTech.
The former is a well-known Russian cybercriminal group and the operator of TrickBot. The latter turned out to be a Russian-speaking organization selling Hermes 2.1 two months before the $58.5 million cyber heist that hit Taiwan's Far East International Bank (FEIB). According to reports, this version of Hermes was used as a decoy or “pseudo-ransomware” simply to distract from the real purpose of the attack.
wizard spider
Recent findings reveal that Wizard Spider has upgraded Ryuk to include a Wake-on-LAN (WoL) utility and an ARP ping scanner in its arsenal. WoL remotely enables network-attached computing devices, regardless of what operating system they are running, when they are powered off, in sleep mode, or in hibernation. It is a network standard that allows you to turn on.
ARP ping, on the other hand, is a method of discovering online endpoints within a LAN network. According to CrowdStrike, these new additions reveal that Wizard Spider is attempting to reach and infect as many of its target endpoints as possible, increasingly monetizing victims' encrypted data. Demonstrates continued focus and motivation.
cryptotech
2 months ago, Gabriela Nicolao (@rove4ever) and Luciano Martins (@clucianomartinsBoth Deloitte Argentina researchers believe that Ryuk ransomware is the work of CryptoTech, a little-known cybercrime group that was observed promoting Hermes 2.1 on underground forums in August 2017. I am. Researchers say Hermes 2.1 is Ryuk ransomware.
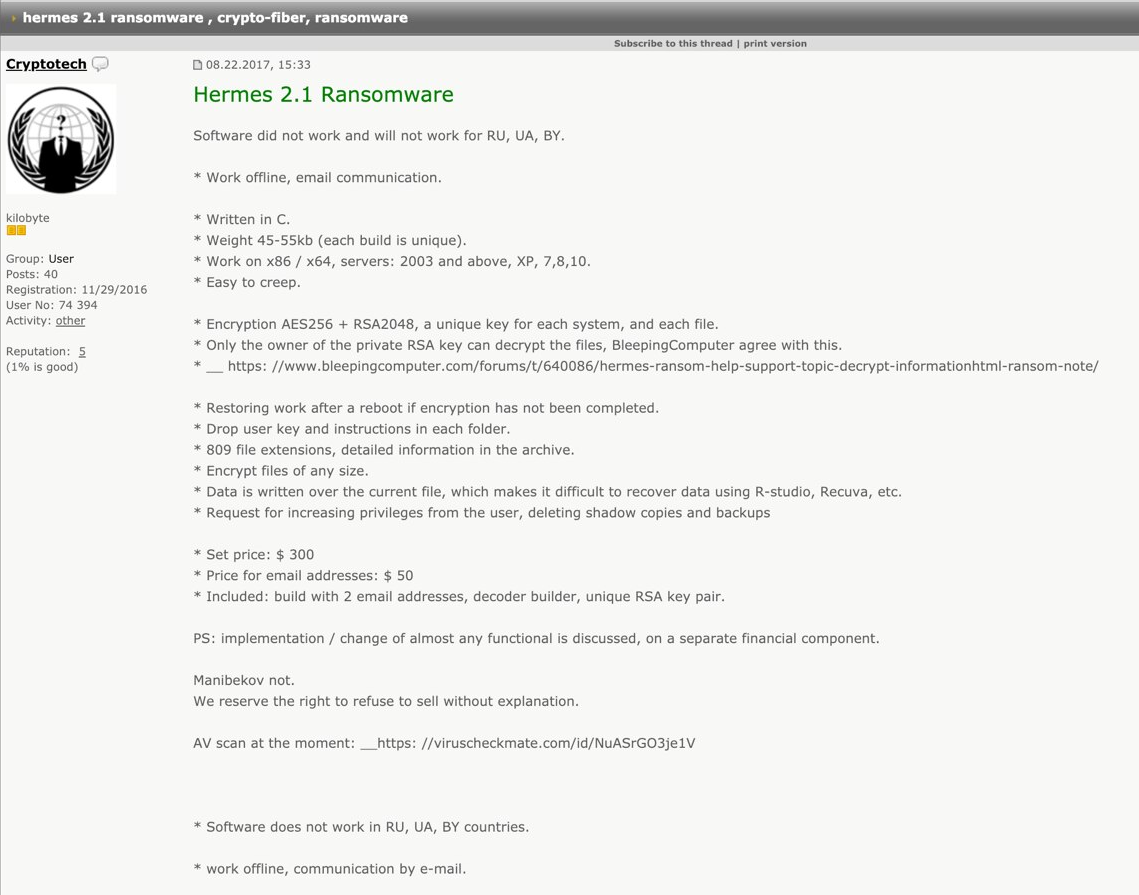
Virus Bulletin conference papers and presentations were titled: Revenge of the Grim Reaper: The Long Tail of Ryuk RansomwareNicolao and Martins presented evidence for this claim: In June 2018, months before Ryuk's first public appearance, posters on an underground forum questioned whether CryptoTech was the author of Hermes 2.1. And before that it was a ransomware toolkit that they had been selling for almost a year. CryptoTech's reaction was interesting, and Nicolao and Martins captured it and annotated the screenshot below.
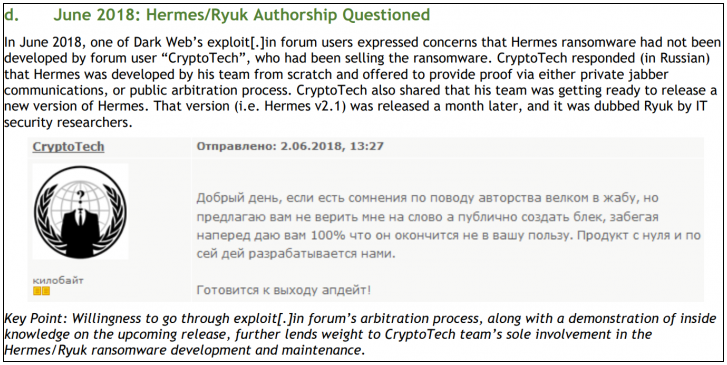
Deloitte researchers also noted that CryptoTech went silent after the emergence of Ryuk.
CrowdStrike estimates that operators have earned a total of 705.80 BTC since Ryuk was introduced until January of this year. This equates to US$5 million at the time of writing.
Ryuk ransomware infection vector
There was a time when Ryuk ransomware invaded clean systems and wreaked havoc. However, the new strain observed in the wild now belongs to multiple attack campaigns, including Emotet and TrickBot. As a result, Ryuk variants reach systems that are pre-infected with other malware. This is a “triple threat” attack method.
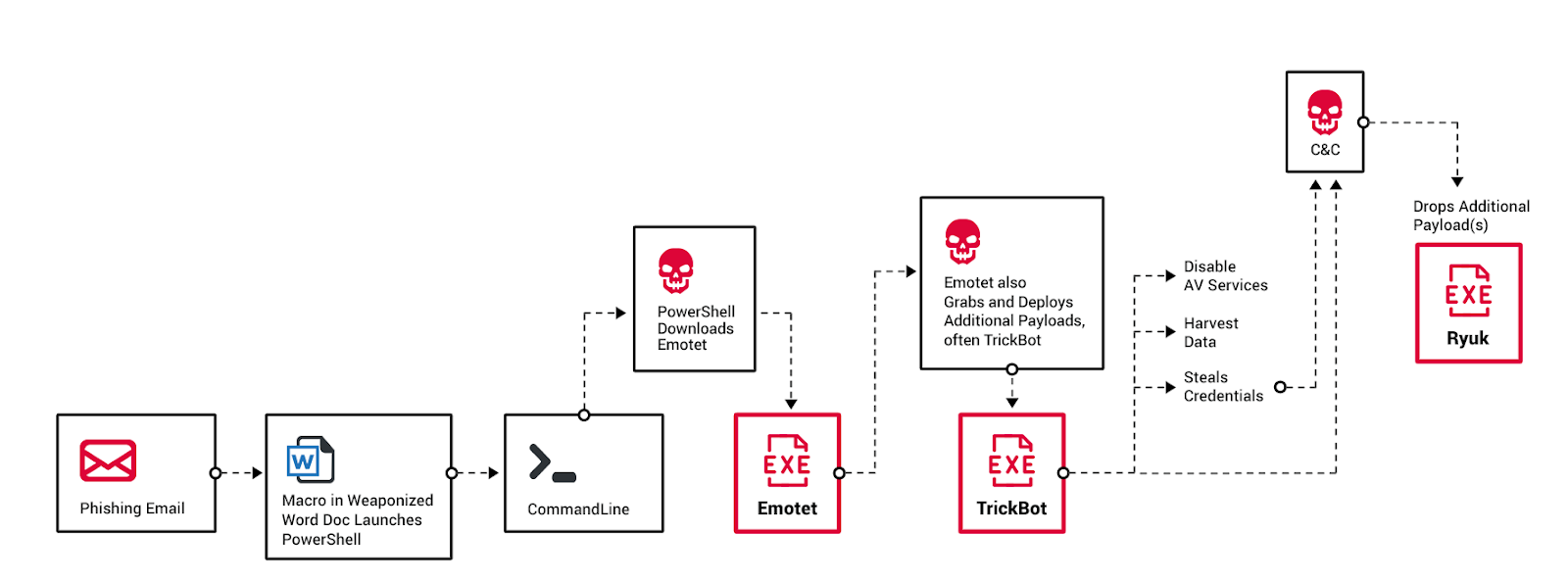
The first stage of the attack begins when a weaponized Microsoft Office document file (containing malicious macro code) is attached to a phishing email. When a user opens it, a malicious macro is executed. cmd Then run the PowerShell command. This command attempts to download Emotet.
Once executed, Emotet retrieves and executes another malicious payload (usually TrickBot) to gather information about the affected system. It begins downloading and running TrickBot by accessing and downloading from a pre-configured remote malicious host.
Once infected with TrickBot, the attacker checks to see if the system is part of the targeted sector. In that case, they download an additional payload and use TrickBot to perform lateral movement using stolen administrator credentials to reach the assets they want to infect.
The threat actor then verifies and establishes a connection to the target's live server via Remote Desktop Protocol (RDP). From there they drop Ryuk.
Symptoms of Ryuk infection
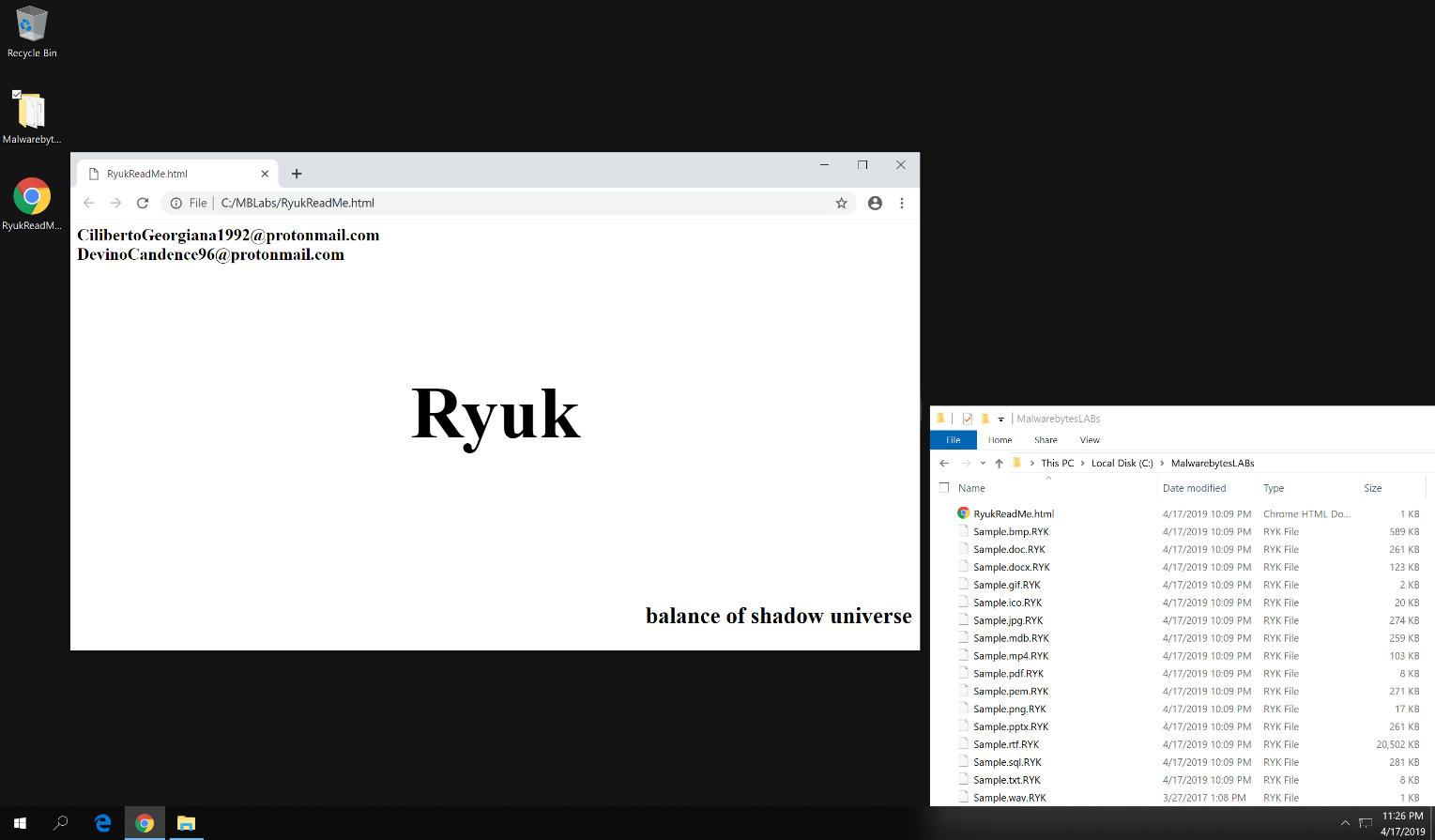
Systems infected with Ryuk ransomware display the following symptoms:
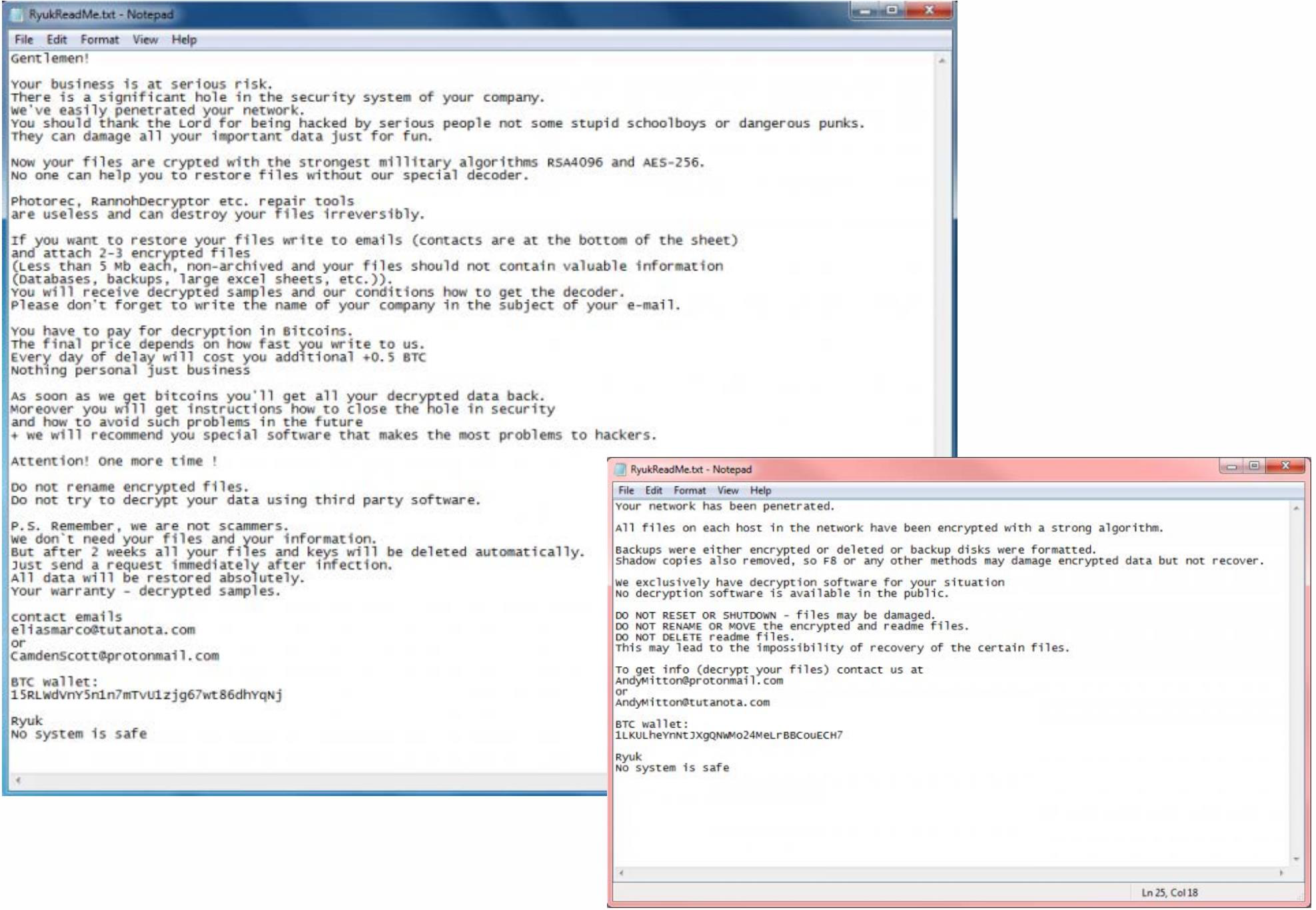
Existence of notes regarding ransomware. Ryuk drops a ransom note. RyukReadMe.html or RyukReadMe.txtin all folders that contain encrypted files.
As you can see from the screenshot above, the HTML file contains two private email addresses that the affected party can use to pay any amount to regain access to their encrypted files. You can find out what you have to pay or contact the attacker. negotiation process.
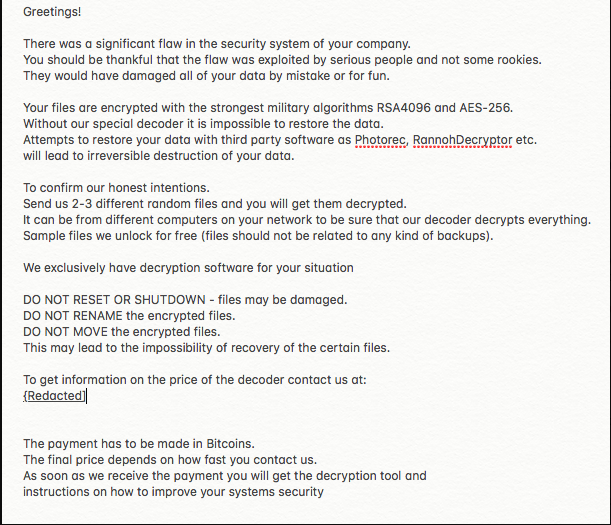
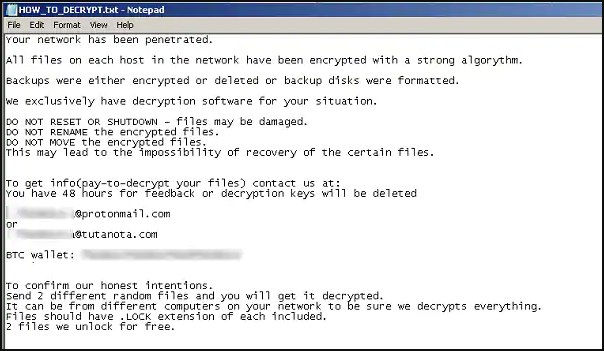
The TXT ransom note, on the other hand, contains (1) explicit instructions for affected parties to read and comply with, (2) two private email addresses that affected parties can contact, and (3) Bitcoin. Contains your wallet address. Note that the email addresses may be different, but they are all accounts provided with Protonmail or Tutanota. Also, a day after the indictment of two ransomware operators was released, the Ryuk operator removed the Bitcoin address from the ransom note and stated that the address would be given to affected people if contacted by email. It got attention.
There are usually two versions of text ransom notes. One is the polite version, which past research claims is equivalent to BitPaymer's because of certain similar expressions. And a less polite version.
Encrypted file with RYK string appended to the extension name. Ryuk encodes files using a combination of symmetric (using AES) and asymmetric (using RSA) encryption. Proper decryption of files requires a private key that only the threat actor can provide.
Encrypted files have a .ryk file extension added to the file name. For example, encrypted sample.pdf and sample.mp4 In the file sample.pdf.ryk and sample.mp4.ryk Each file name.
This scheme is effective given that Ryuk strains are customized to each target organization.
Ryuk encrypts files on affected systems, but avoids files with the extensions .exe, .dll, and .hrmlog (file types associated with Hermes). Ryuk also avoids encryption of files in the following folders:
- unlab
- chromium
- microsoft
- Mozilla
- recycle.bin
- window
Protect your system from Ryuk
Malwarebytes continues to track Ryuk ransomware campaigns and protect business users with real-time anti-malware and anti-ransomware technology, and signature-less detection that stops attacks early in the attack chain. Additionally, blocking Emotet or TrickBot downloads protects against triple-threat attacks aimed at delivering Ryuk as the final payload.
We recommend that IT administrators take the following steps to protect and mitigate Ryuk ransomware attacks.
- Educate all employees in your organization, including executives, on how to properly handle suspicious emails.
- Limit the use of privileged accounts to a select few people within your organization.
- Avoid using RDP without properly terminating the session.
- Implement the use of password managers and single sign-on services for company-related accounts. Eliminate other insecure password management methods.
- Implement a certification process that is appropriate for your company.
- Disable unnecessary shared folders to prevent malware from moving laterally within your network in the event of a Ryuk ransomware attack.
- Ensure all software installed on endpoints and servers is up to date and patched for all vulnerabilities. Be especially careful when patching CVE-2017-0144, a remote code execution vulnerability. This prevents the spread of TrickBot and other malware that exploit this vulnerability.
- Apply attachment filtering to email messages.
- Disable macros for the entire environment.
For a list of technologies and operations found to be effective against Ryuk ransomware attacks, go here.
Indicators of Compromise (IOC)
Please note that professional cybercriminals sell Ryuk on the black market to other criminals as a toolkit for threat actors to build their own ransomware. So we shouldn't be surprised at the number of Ryuk subspecies wreaking havoc in the wild. Below is a list of file hashes that we have reviewed so far.
- cb0c1248d3899358a375888bb4e8f3fe
- d4a7c85f23438de8ebb5f8d6e04e55fc
- 3895a370b0c69c7e23ebb5ca1598525d
- 567407d941d99abeff20a1b836570d30
- c0d6a263181a04e9039df3372afb8016
As always, everyone stay safe!

