
EXECUTIVE SUMMARY
At CYFIRMA, we provide timely insights into prevalent threats and malicious tactics affecting organizations and individuals. Our research team have identified an open directory listing URLs containing highly obfuscated malicious Windows batch scripts in the wild, which executes a stealthy Monero (XMR) crypto miner as the final payload.
This payload is unfolded after 5 stages of unpacking, with capabilities such as Anti analysis /debugging, privilege escalation, defense evasion, stealth execution, file-less execution, and mining cryptocurrency. This malware has a very low to zero malicious reputation on known anti-malware tools.
Our investigation determined that the victims of this miner are distributed across multiple countries, notably India, USA, and Russia, generating approximately $750 USD in illicit profits over the last 40 days. The malware appears to undergo frequent updates, with new iterations released every few days. The malicious activity associated with this malware strain has been ongoing since February 29, 2024, and continues to date.
INTRODUCTION
We have identified an open indexed directory hosted on an Apache web server at URL: ‘hxxp[:]//89[.]23[.]97[.]199[:]1444/’ and ‘hxxps[:]//89[.]23[.]97[.]199/’ which hosts multiple windows batch scripts. There, we identified three obfuscated malicious windows batch scripts named ‘Anonmy (variant 1).cmd’, ‘Anonmy (variant 2).cmd’, and ‘project88.cmd’.
After an in-depth analysis of these malicious samples, we have concluded this is a ‘Crypto Miner Malware’ that specifically mines Monero (XMR) cryptocurrency. This miner malware is obfuscated, executing its final payload after five stages of unpacking and de-obfuscation. While unfolding to the final payload, miner malware implements techniques like anti-analysis/debugging, Privilege Escalation, Defense Evasion, Stealth execution, and file-less execution.
When the threat actors utilize computing resources without authorization for cryptocurrency mining, it is referred to as ‘cryptojacking’. Generally, these cryptojacked machines are high-end CPU or GPU-based servers used by organizations to run their day-to-day operations. After cryptojacking, these machines face serious performance issues as most of the computing resources are used to mine cryptocurrency via malware – posing a significant risk to the organizations.
Multiple stages of this malware are demonstrated below:
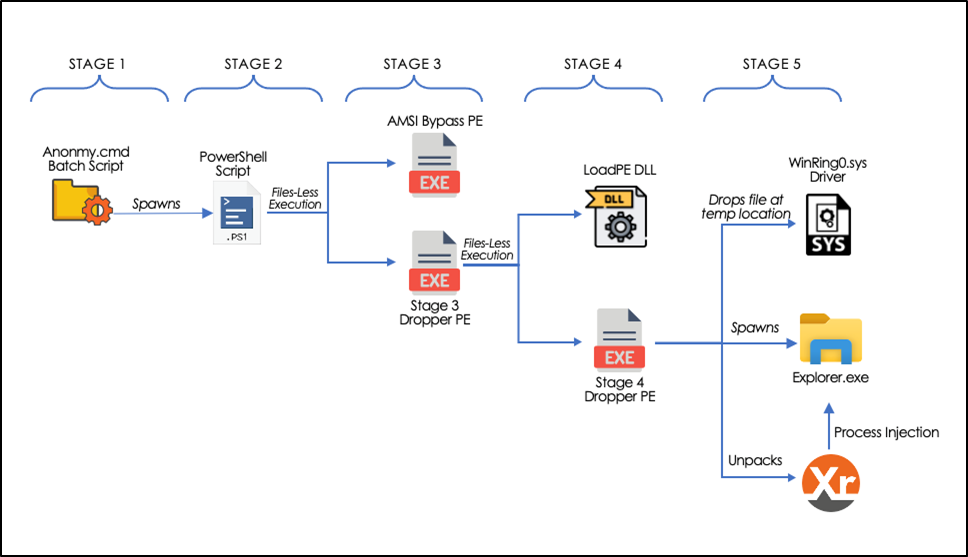
Figure 1
To summarize the execution flow, the malicious batch script [Stage 1] is executed to spawn an obfuscated PowerShell script [Stage 2]. This PowerShell script further drops and executes two more Portable Executable (PE) files [Stage 3]. One of these PE files further drops and executes two additional PE files [Stage 4] which in turn spawns the final payload ‘XMR crypto miner’.
During our analysis, we did not identify any persistence mechanism implemented at any stage, meaning that it is likely that persistence has been implemented by threat actors before the execution of batch scripts. Let’s assume a scheduled task, or a system service, could have been set up on a compromised system to download the latest updated batch script from the identified open indexed URL, with every restart of the system: this way, persistence would be the ideal choice for threat actors as this miner malware is updated within a few days.
We will discuss these multi-level de-obfuscations, and how the malware uses several techniques to evade defense mechanisms, escalate privileges, perform file-less execution, and apply anti-analysis / debugging methods in the ‘Analysis’ section of this report.
KEY POINTS
- Malicious batch script is stored on an Open indexed directory at URL: ‘hxxp[:]//89[.]23[.]97[.]199[:]1444/’ and ‘hxxps[:]//89[.]23[.]97[.]199/’, which seems to be updated every few days. The last updated iteration of malware was identified on April, 04 2024.
- Three variants of this miner malware have been observed, all of which de-obfuscate and unfold using similar techniques, dropping files with different hashes – files like PowerShell script, PE files, and DLL files.
- Miner malware operates stealthily in the background, and has capabilities to impair defense systems by techniques like privilege escalation, process injection, AMSI bypass, file-less execution, obfuscation, and multi-stage execution. Also, malware implements various anti-analysis/debugging techniques during various stages of execution.
- This miner malware has been active at least since February, 29, 2024, with victims distributed across multiple countries (however 36% are from Iran, 8% from India, 6.4% from USA, and 5.5% from Russia).
- Victims of this miner malware are minting approximately 570 KH/s [Computing Power] which can mine approximately $500 USD per month worth of XMR coins. This malware has a very low to zero malicious reputation on the known anti-malware tools, so victims may fall prey to this in near future.
ETLM ATTRIBUTION
The Cyfirma research team consistently explores emerging threats, malware, and Tactics, Techniques, and Procedures (TTPs) employed by threat actors. We actively monitor existing threats, track ongoing campaigns, assess their progress, and stay vigilant for any novel developments within this landscape.
Building on these ongoing efforts, we have uncovered a recent malicious batch script hosted on the open indexed directory at URL: ‘hxxp[://]89[.]23[.]97[.]199:1444/’ and ‘hxxps[://]89[.]23[.]97[.]199/’:
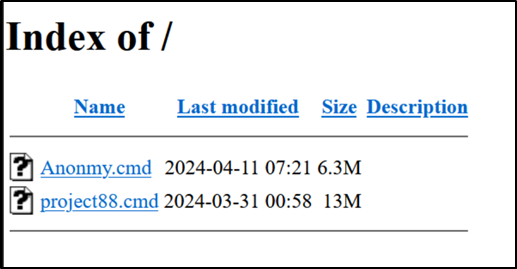
Figure 2
Script ‘Anonmy.cmd’ was last updated on the server on April 11, 2024, indicating that frequent updates are pushed on the server within every few days.
The server IP address ‘89[.]23[.]97[.]199’ is hosted in Russia, and has a very low reputation with well-known anti-malware tools. Similarly, PE files, DLL files, and PowerShell script has no known malicious reputation by these well-known anti-malware tools.
The final payload dropped by this miner malware is identified as Monero (XMR) cryptocurrency miner (XMRrig.exe). Monero mining is usually done by utilizing the system’s CPU resource which solves complex math problems: generally, mining is performed using a mining pool – a group of miners who connect their computing resources over a network.
In this case, the ‘hxxps[://]monero[.]hashvault[.]pro/’ mining pool is used, and the pool’s dashboard is only available in English and Russian.
Furthermore, in our analysis we identified a total of three XMR wallet addresses. Two of these three addresses are directly linked to the threat actor, while the third one is not directly associated. OSINT analysis for the third XMR wallet address reveals this address belongs to ‘hackforum[.]net’ user ‘UnamSanctam’ refer thread ‘hxxps[:]//hackforums[.]net/showthread.php?tid=5995773’:
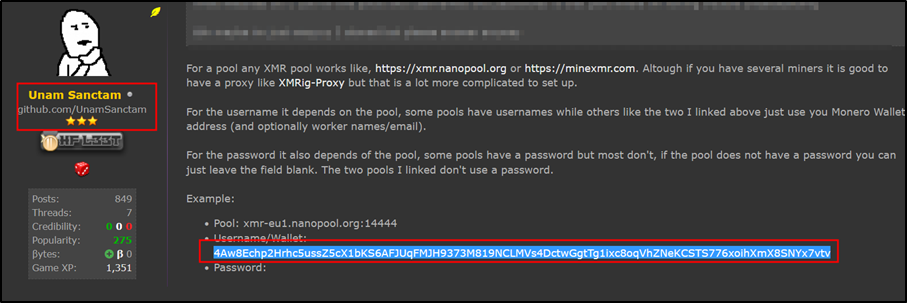
Figure 3
This identified ‘hackforums[.]net’ user is linked with a GitHub profile: ‘hxxps[:]//github[.]com/UnamSanctam/’. The same GitHub user hosts a repository called ‘SilentCryptoMiner’, which claims to be a stealthy XMR crypto miner (Figure 4). This clearly indicated that the final payload of this miner malware is a variant of ‘SilentCryptoMiner’, hosted on GitHub.

Figure 4
The ‘SilentCryptoMiner’ repository is freely available on GitHub, and comes with a builder by the name ‘Silent Crypto Miner Builder 3.4.0’ executable, which can build a customizable XMRrig.exe miner with several customizations (like operating covertly, identifying and killing malware analysis tools, and building random static signature:
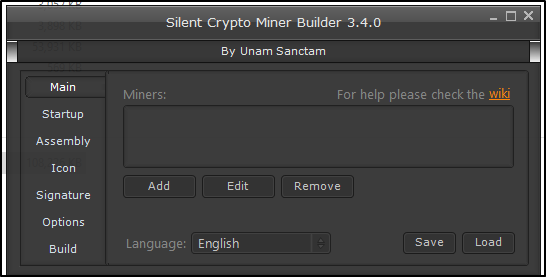
Figure 5
It is common practice among miner developers to embed developers’ crypto wallet addresses in mining software. A portion of the mined cryptocurrency is then directed to these developer addresses. The GitHub repository and Open indexed URL are both last updated on the same date (April, 11, 2024), however this may be a coincidence.
The other two XMR wallet addresses identified during analysis are associated with the threat actor, and are used to receive the mined cryptocurrency coins. A total of 6.436 XMR had been mined in the last forty days, with the first payment received on February, 29, 2024 at 23:33:43 UTC at the mining pool (see Figures 6.1 and 6.2).

Figure 6.1

Figure 6.2
As mentioned above, victims of this miner malware are distributed among multiple countries across globe, Figure 7 demonstrates the demographics of network traffic towards the malware.
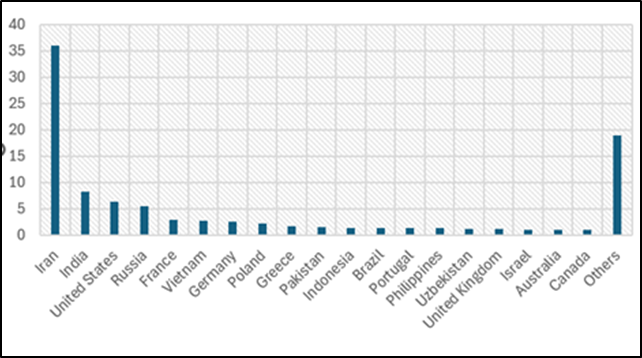
Figure 7
As per our investigation, we are not attributing the malware to any particular threat actor.
ANALYSIS:
Basic Details:
| File Name | Anonmy.cmd |
| File Type | Windows Batch Script |
| Size | 7.52 MB (7,894,210 bytes) |
| MD5 | a4fe3e69c2f52e38a34722d28e6423d4 |
| SHA256 | b5a008e84b04f2d8c4dfc0451d1473e7514eecf5c2d5bf3e0c0881b3141bf7f8 |
| Date Modified | 2024-04-11 |
The contents of the ‘Anonmy.cmd’ script clearly show that the script is heavily obfuscated. There are more than 10,000 lines present in the script, and among them most of them are comments in the batch script that start with either “REM” or “::”. After removing all the comments from the batch script, the remaining script lines are shown in Figure 8.
Part 1, highlighted in Figure 8, shows variables ‘cJouWu’, ‘YDnfPn’ and ‘aSHpwO’ that are initialized with obfuscated strings. The search and replace function is then performed on all these strings, where the string “VzUey” is replaced with the empty string – after these replacements are de-obfuscated, the string is executed.

Figure 8
Figure 8.1, represents de-obfuscated code of part 1 in Figure 8. This initializes variable ‘MkoE’ with value 1, and re-executes the Anonmy.cmd script in a minimized command prompt. When ‘Anonmy.cmd’ script is re-executed, part 1 of Figure 8 is not executed again.

Figure 8.1
The highlighted part 2 of Figure 8 shows variables ‘pYnWEg’, ‘nxmLoS’ , ‘aPiOJb’, and ‘vUAkXo’ are initialized with obfuscated strings, similar to part 1 search and replace function is executed to perform de-obfuscation.
Figure 8.2 shows the final payload which is executed after de-obfuscating part 2. This line echoes a long obfuscated string and pipes it to stdin of executable ‘C:\Windows\System32\WindowsPowerShell\V1.0\powershell.exe’, the echoed string is nothing but an obfuscated PowerShell script.

Figure 8.2
The PowerShell script is obfuscated, however we have de-obfuscated it and replaced the names of a few variables and functions with more relevant names for better readability (Figure 9). This script opens the file ‘Anonmy.cmd’ to read the contents of particular line which starts with “::” – these lines are comments in context to batch script. These lines are first base64 decoded, and then passed as an argument to func1(). The return value of func1() is passed as an argument to func2(): the return value of func2() is bytes array, which is stored in a variable.
‘func1()’ in PowerShell Script is used to decrypt a given input using the AES algorithm, however the KEY and IV used for decryption are also present in this function (see the part 1, Figure 9).
‘func2()’ is used to uncompress a ‘gzip’ compressed stream and return a bytes array.
These returned bytes array is nothing but a Portable Executable (PE) binary. We will refer to these decrypted PE binaries as ‘stage 3-1 AMSI bypass.exe’ PE and ‘stage 3-2 dropper.exe’ PE. Now PowerShell script executes both PE binary 1 by 1, which are performed directly in memory, (i.e. file-less execution).
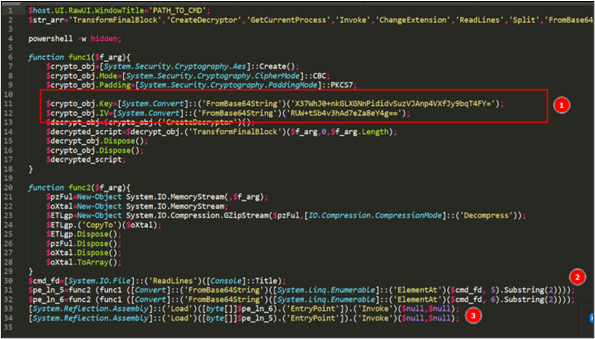
Figure 9
Basic details for Stage 3-1 AMSI bypass.exe
| File Type | PE32 |
| Subsystem | Console |
| File Size | 10.5 KB (10,752 bytes) |
| Compiler Timestamp | 2024-04-04 22:15:53 UTC |
| MD5 | ddaaa8d00a819594a54946bd0be99eb5 |
| SHA256 | e656be193c3170d1838e13bdce48e708a2b15076d536a0e9bfacf3f366c62a51 |
‘Stage 3-1 AMSI bypass.exe’ is a dotNet compiled binary. Using tools like dnSPY, we can view the source code of the binary (see Figure 10).
The purpose of stage 3-1 PE binary is to bypass Antimalware Scan Interface (AMSI) scanning to impair the defense system.
In Windows OS, ‘AMSIScanBuffer()’ function – defined in ‘AMSI.dll’ – is responsible for scanning the code before execution to determine whether it is malicious before execution.
According to Microsoft, documentation for ‘AMSIScanBuffer()’ function scans the string ‘buffer’ of size ‘length’ before execution. The stage 3-1 PE binary bypasses AMSI scans by patching function ‘AMSIScanBuffer()’ straight in the memory. Bytes ‘{184, 87, 0, 7, 128, 195}’ are used to patch the function – simply by setting the ‘length’ value to zero, the scan will be performed on input string of length zero.

Figure 10
After execution of ‘Stage 3-1 AMSI bypass.exe’, the PowerShell script executes ‘Stage 3-2 dropper.exe’.
Basic details for Stage 3-2 dropper.exe
| File Type | PE32 |
| Subsystem | Console |
| File Size | 4.74 MB (4,973,056 bytes) |
| Compiler Timestamp | 2024-04-04 22:15:52 UTC |
| MD5 | 84864dd9b923cd223aad9852c806b3cd |
| SHA256 | 2db5b28fe6d694f6d064edd3713e701aa19725ae6de31c796d00dcb0c6e6ad1b |
This ‘Stage 3-2 dropper.exe’ binary is also a dotNet compiled binary (refer to its source code in Figure 11). This PE binary is a dropper, which further drops more PE files for execution.
Part 1 of Figure 11 shows the executable has implemented anti debugging/ analysis techniques, demonstrating the ability to check if a remote or local debugger is attached to the running process.
Part 2 of Figure 11 shows that the binary stores 2 more PE binaries, compressed using the gzip algorithm and stored inside the resource section named ‘P’ and ‘LP’ (the stored PE binaries are uncompressed and executed).
Resource section ‘LP’ stores a PE DLL named ‘LoadPE.dll’, and section ‘P’ stores a PE binary which will further drop more PE files for execution.
Using dotNet’s function ‘Assembly.Load(),’ resource ‘LP’ (LoadPE.dll) is loaded into memory, and method Run() from ‘LoadPE.LoadPE’ class is executed. LoadPE.LoadPE.Run() performs fileless execution of PE binary stored in resource section ‘P’.
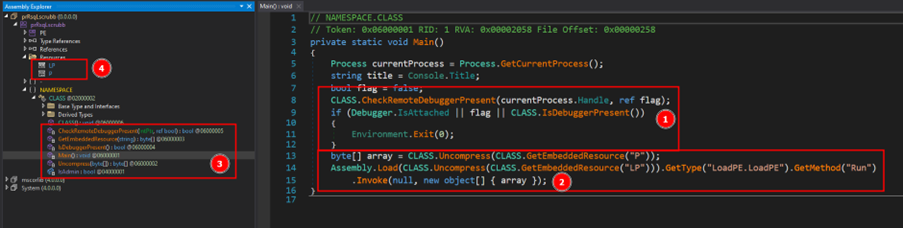
Figure 11
Figure 12 shows the resource section which stores compressed PE files. Let’s refer to these resource section PE files as ‘stage 4 LoadPE.dll’ and ‘stage 4 dropper.exe’.
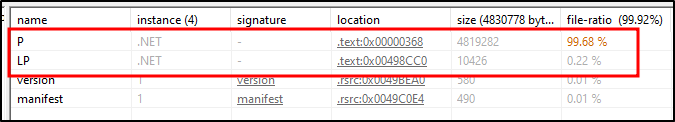
Figure 12
Basic details for Stage 4 LoadPE.dll
| File Type | PE32 DLL |
| Subsystem | Console |
| File Size | 321 KB (329,216 bytes) |
| Compiler Timestamp | 2044-05-31 11:08:27 UTC |
| MD5 | aed04cc22f8d4cc2bc6f0b07ee1d3c33 |
| SHA256 | 51df1afc471e8f4805293b251acfa72c41f9b1ca67459df419440a1c65156059 |
This DLL is dotNet compiled code, Figure 13 shows the source code. The purpose of this is to load and execute ‘stage 4 dropper.exe’, which is performed using the function ‘MemoryCallEntryPoint()’ of C# library ‘DLLFromMemory’ to achieve file-less execution.
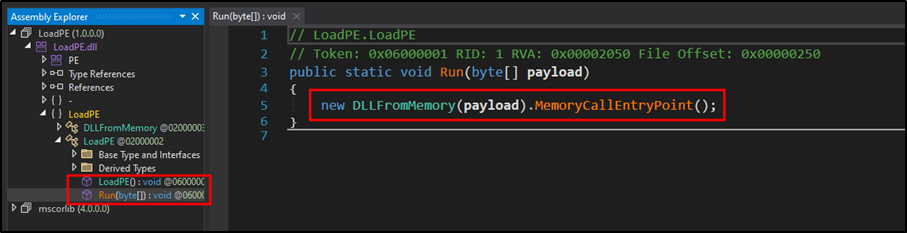
Figure 13
Basic details for Stage 4 dropper
| File Type | PE64 |
| Subsystem | GUI |
| File Size | 6.84 MB (7,174,144 bytes) |
| Compiler Timestamp | 2024-04-04 15:06:56 UTC |
| MD5 | ed3dc99329202fa901203b8100643357 |
| SHA256 | 37af3dd3964b98a4296a266ef4ca71febd61755c9e7a248bc05a5b5ce5be91dc |
This ‘stage 4 dropper.exe’ contains an obfuscated assembly code. On execution, it drops a Windows sys driver, ‘WinRing0.sys’, and also performs process injection into legitimate Windows process ‘explorer.exe’ to inject a cryptocurrency miner PE ‘XMRrig.exe’. This miner is first decrypted in memory and then injected into ‘explorer.exe’ after performing process injection ‘stage 4 dropper.exe’ exits.
‘WinRing0.sys’ driver is dropped at temp location ‘C:\Users\user\AppData\Local\Temp\eolmboqmufeo.sys’, with random file name ‘eolmboqmufeo.sys’ (see Figure 14). This SYS file is XMRrig.exe cryptominer’s Windows driver. We will refer to this temp SYS file as ‘stage 5 WinRing0.sys’

Figure 14
Figure 15 shows the spawning of the legitimate Windows process ‘explorer.exe’\

Figure 15
Using a debugger, we identified before execution of function ‘sub_7ff6967E155D’, the bytes of PE ‘XMRrig.exe’ are stored in process memory, and register RAX points to these PE bytes (see Figure 16).
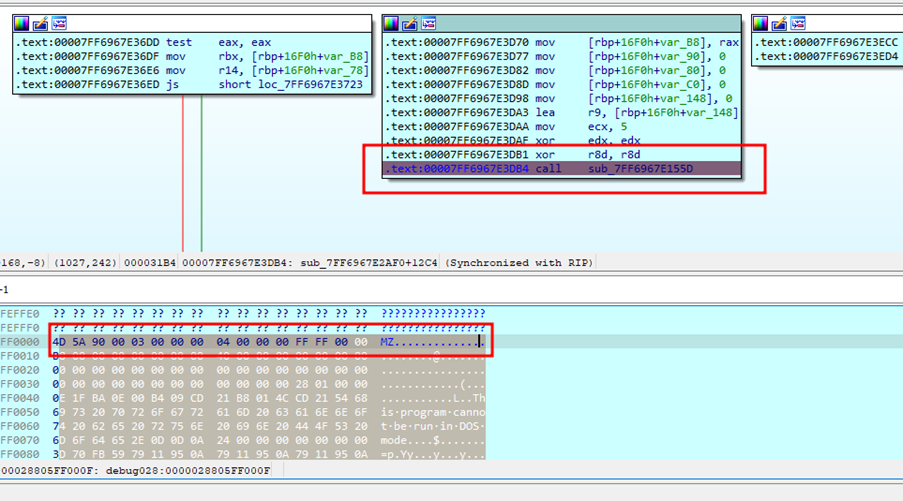
Using the following IDA IDC script, we dumped the bytes representing this PE file for further analysis. Variable ‘rax_addr’ is set to the value of RAX register, so we dumped approximately 10MB+ of bytes to extract the PE file in memory.
auto file = “C:\\Users\\Public\\dump.bin”;
auto rax_addr = 0x197517E0000; // value of RAX register
auto sz = 0xb00000; // target file is approximately 10 MB in size
auto fd = fopen(file, “wb”);
savefile(fd, 0, rax_addr, sz);
fclose(file);
Tools like ‘binwalk’ can be used to extract the exact PE file from the file ‘dump.bin’. We will refer to this extracted PE file as ‘stage 5 XMRrig.exe’.
After process injection, ‘stage 4 dropper.exe’ exits.

Figure 16
Basic details for Stage 5 WinRing0.sys
| File Type | PE64 |
| Subsystem | Native |
| File Size | 14.2 KB (14,544 bytes) |
| Compiler Timestamp | 2008-07-26 13:29:37 UTC |
| MD5 | 0c0195c48b6b8582fa6f6373032118da |
| SHA256 | 11bd2c9f9e2397c9a16e0990e4ed2cf0679498fe0fd418a3dfdac60b5c160ee5 |
File ‘WinRing0.sys’ is dropped in the temporary location with a random name, in this case, ‘eolmboqmufeo.sys’. ‘WinRing0.sys’ is also part of the official XMRrig miner release (see https://github.com/xmrig/xmrig/tree/master/bin/WinRing0).
XMRrig miner, available on Git Hub, is a cryptominer tool used to mine Monero cryptocurrency, however the tool itself does not have capabilities to run covertly or perform any kind of malicious activity such as process injection.
Driver ‘WinRing0.sys’ is used by XMRrig.exe to access CPU MSR registers, read/write memory directly, and elevate privileges.
Basic details for Stage 5 XMRrig.exe
| File Type | PE64 |
| Subsystem | GUI |
| File Size | 11.0 MB (11,534,336 bytes) |
| Compiler Timestamp | 2023-10-13 20:52:10 UTC |
| MD5 | 0282de7d55c591fea67ecb0629bfc78d |
| SHA256 | b531b2e06b0d3bafabad968f28a255eeb61132dc3eafd76680d16e280790a5fe |
This is the final payload of this crypto miner malware, and upon execution, it starts mining cryptocurrency to a configured XMR wallet address via a mining pool.
Upon reviewing the process memory, we identified that this process is executed with the below given command line arguments, which contain the XMR wallet address and mining pool URL.
explorer.exe –algo=rx/0 –url=pool[.]hashvault[.]pro:80 –user=”43dA79px7SY67JTEJm36wAAGVgERQMvWSbpeYxEriWrsAgDdqnL6g4LXAFHcu1TfUe9zmRyuLBe1XL6Gc6gjNRqdVE9h9HR” –pass=”Xeon” –cpu-max-threads-hint=50 –cinit-winring=”eolmboqmufeo.sys” –cinit-stealth-targets=”Taskmgr.exe,ProcessHacker.exe,perfmon.exe,procexp.exe,procexp64.exe” –cinit-version=”3.4.0″ –tls –cinit-idle-wait=3 –cinit-idle-cpu=90 –cinit-id=”vflprbupfwpyhduu”
As mentioned in the above sections, there are more variants to this miner malware hosted on the same identified URL. The following snippets are the other command line options observed from different variants.
explorer.exe –algo=rx/0 –url=pool.hashvault.pro:80 –user=”44KVH1GsLoQKo3SopPutFeNBZn9mH1JwS6BPqAqDzbSWTSGsTtqH6WoMoVRv4bBr5RAKgp21jgPAiRnXWZWjgQuUDrKECFw” –pass=”worker1″ –cpu-max-threads-hint=50 –cinit-winring=”vsropqoqruue.sys” –cinit-stealth-targets=”Taskmgr.exe,ProcessHacker.exe,perfmon.exe,procexp.exe,procexp64.exe” –cinit-version=”3.4.0″ –tls –cinit-idle-wait=3 –cinit-idle-cpu=90 –cinit-id=”ljqkcljscuiqwpvp”
explorer.exe –algo=rx/0 –url=pool.hashvault.pro:80 –user=”43dA79px7SY67JTEJm36wAAGVgERQMvWSbpeYxEriWrsAgDdqnL6g4LXAFHcu1TfUe9zmRyuLBe1XL6Gc6gjNRqdVE9h9HR” –pass=”Ryzen” –cpu-max-threads-hint=50 –cinit-winring=”ehldbgrngqrt.sys” –cinit-stealth-targets=”Taskmgr.exe,ProcessHacker.exe,perfmon.exe,procexp.exe,procexp64.exe” –cinit-version=”3.4.0″ –tls –cinit-idle-wait=3 –cinit-idle-cpu=90 –cinit-id=”mfshepiebtdyqslg”
The above-given command line options clearly show the malware further implements another anti-analysis technique by further scanning for malware analysis tools like ‘Taskmgr.exe, ProcessHacker.exe, perfmon.exe, procexp.exe, and procexp64.exe’ running in the system, and tries to kill them.
The identified XMR wallet address in the above command line arguments ‘43dA79px7SY67JTEJm36wAAGVgERQMvWSbpeYxEriWrsAgDdqnL6g4LXAFHcu1TfUe9zmRyuLBe1XL6Gc6gjNRqdVE9h9HR’ and ‘44KVH1GsLoQKo3SopPutFeNBZn9mH1JwS6BPqAqDzbSWTSGsTtqH6WoMoVRv4bBr5RAKgp21jgPAiRnXWZWjgQuUDrKECFw’ are the threat actor’s wallet address, where mined XMR cryptocurrency are received.
Further analysis revealed 1 more XMR wallet address is stored in ‘stage 5 XMRrig.exe’ : ‘4Aw8Echp2Hrhc5ussZ5cX1bKS6AFJUqFMJH9373M819NCLMVs4DctwGgtTg1ixc8oqVhZNeKCSTS776xoihXmX8SNYx7vtv’ which is linked to GitHub user ‘UnamSanctam’ .
This miner malware mines Monero (XMR) cryptocurrency by using victims’ computational resources without authorization. Monero offers enhanced privacy features compared to Bitcoin: transactions made with Monero are untraceable, making it attractive for threat actors. Monero mining does not require specialized hardware like other cryptocurrency miners, so it can effectively use regular computers, making it accessible to a wider range of attackers.
Upon execution of one of the batch script following process tree is observed (see Figure 19).

Figure 19
CONCLUSION
Our research reveals a sophisticated cyber threat distributed through an open indexing directory web page, which operates in stealthy mode, with the threat actor implementing various protective techniques such as like defense evasion and anti-analysis/debugging. The malware code is updated every few days, producing different signatures to bypass static detection, which was probably developed by a builder for this purpose to automate the long process of packing multiple stages together into a batch script.
Based on the new XMR wallet address [which links to user ‘UnamSanctam’] found in ‘Stage 5 XMRrig.exe’ we have concluded the ‘stage 5 XMRrig.exe’ (the final payload in the miner malware) can be a variant of ‘SilentCryptoMiner’ – GitHub, which in turn is a variant of official XMRrig miner ‘https://github.com/xmrig/xmrig’.
We have identified a total of three variants of this malicious batch script (miner malware) on the same identified open directory URL, all of which de-obfuscate in a similar way during all five stages (we have documented IOCs from all three variant of batch script in IOC section below).
This miner malware has been active at least since February, 29, 2024, and has cryptojacked many machines which are minting approximately 570 Kilo Hash / second.
We speculate that more machines will be cryptojacked by this malware to contribute to the rising computing power, resulting in more illicit profits for cybercriminals.
The campaign demonstrates a sophisticated grasp of obfuscation methods and dynamic script execution. In summary, this report highlights the complex and multi-step strategies employed by threat actors, emphasizing the need for proactive cybersecurity measures to mitigate advanced threats.
LIST OF IOCS
| Sr. No. | Indicator | Type | Remarks |
| 1 | 89[.]23[.]97[.]199 | IP Address | Open indexing directory |
| 2 | pool[.]hashvault[.]pro | Domain | Mining Pool address |
| 3 | 43dA79px7SY67JTEJm36wAAGVgERQMvWSbpeYxEriWrsAgDdqnL6g4LXAFHcu1TfUe9zmRyuLBe1XL6Gc6gjNRqdVE9h9HR | XMR wallet address | Threat actor’s wallet address 1 |
| 4 | 44KVH1GsLoQKo3SopPutFeNBZn9mH1JwS6BPqAqDzbSWTSGsTtqH6WoMoVRv4bBr5RAKgp21jgPAiRnXWZWjgQuUDrKECFw | XMR wallet address | Threat actor’s wallet address 2 |
| 5 | 4Aw8Echp2Hrhc5ussZ5cX1bKS6AFJUqFMJH9373M819NCLMVs4DctwGgtTg1ixc8oqVhZNeKCSTS776xoihXmX8SNYx7vtv’ | XMR wallet address | Wallet address associated with user ‘UnamSanctam’ |
| 6 | ad822713a862cb63a907473fdadab453be8a52be | SHA1 Hash | Anonmy.cmd |
| b5a008e84b04f2d8c4dfc0451d1473e7514eecf5c2d5bf3e0c0881b3141bf7f8 | SHA256 Hash | ||
| a4fe3e69c2f52e38a34722d28e6423d4 | MD5 Hash | ||
| 7 | 782883a4d905930639fed43e65ebd68e165f41ba | SHA1 Hash | project88.cmd |
| 8eae2e431412e59daf4c20c05a6cfcdfbe84a6cb4739e2964ab8cfc74df6a92f | SHA256 Hash | ||
| 8799ef3b57d0e76211bfd01a55d29f01 | MD5 Hash | ||
| 8 | 79525044e5a0d21fb453990981796e9af337a157 | SHA1 Hash | Stage 3 AMSI bypass.exe – 1 |
| af6577428fbd2e28ef95a7a3b3cf89f833d7e2ac457b999e1905e0d0c1477132 | SHA256 Hash | ||
| 59756d324c2d605d4cee59d5c4671ff7 | MD5 Hash | ||
| 9 | f71cb2f03385f80e8e42830ead296d2e503c5971 | SHA1 Hash | Stage 3 AMSI bypass.exe – 2 |
| e656be193c3170d1838e13bdce48e708a2b15076d536a0e9bfacf3f366c62a51 | SHA256 Hash | ||
| ddaaa8d00a819594a54946bd0be99eb5 | MD5 Hash | ||
| 10 | ee0c1f07fe2630a1871a7154961ecf3ab426dc1f | SHA1 Hash | Stage 3 AMSI bypass.exe – 3 |
| e45b0d801c435ae25fe9596c97f45aeb096f70b9fd3f8244c9bb7d85ed094c11 | SHA256 Hash | ||
| 952138ef10f6d3814ed5888a4baa63cc | MD5 Hash | ||
| 11 | da6a98df294b4d7c54f2af93d178b733d90c626e | SHA1 Hash | Stage 3 dropper.exe – 1 |
| 3fc0286c2fc31538344011001eaad44073b0440ad857b97b0a84c7dbb670f231 | SHA256 Hash | ||
| 53e94b9b26ea1c1692a718c31fba8c14 | MD5 Hash | ||
| 12 | 509b94234bf0c1e20e60770628a45e60aa6691ee | SHA1 Hash | Stage 3 dropper.exe – 2 |
| 2db5b28fe6d694f6d064edd3713e701aa19725ae6de31c796d00dcb0c6e6ad1b | SHA256 Hash | ||
| 84864dd9b923cd223aad9852c806b3cd | MD5 Hash | ||
| 13 | 3fd88848783c0715b19bcb9928f397340176e3d9 | SHA1 Hash | Stage 3 dropper.exe – 3 |
| 84c1f4a43af3837294039bd3cb86c7c93f2bdfd39b19bad6e6cd7ba1c458dc7a | SHA256 Hash | ||
| f2a03b36a0699b186f2e4b2e613b5f86 | MD5 Hash | ||
| 14 | 636b630682257397891b9b16d68346c689e47a9a | SHA1 Hash | Stage 4 LoadPE.dll – 1 |
| 51df1afc471e8f4805293b251acfa72c41f9b1ca67459df419440a1c65156059 | SHA256 Hash | ||
| aed04cc22f8d4cc2bc6f0b07ee1d3c33 | MD5 Hash | ||
| 15 | 636b630682257397891b9b16d68346c689e47a9a | SHA1 Hash | Stage 4 LoadPE.dll – 2 |
| 51df1afc471e8f4805293b251acfa72c41f9b1ca67459df419440a1c65156059 | SHA256 Hash | ||
| aed04cc22f8d4cc2bc6f0b07ee1d3c33 | MD5 Hash | ||
| 16 | af05b9ff6cd94a945dcd1646347c32f3c88bbc41 | SHA1 Hash | Stage 4 LoadPE.dll – 3 |
| 84372edb46a92d3dac855bcc54e5fd002b62f3c785f06051710a63ff754d6ef5 | SHA256 Hash | ||
| 7b7f17bbd599bfb44ea76430aeb6d6d4 | MD5 Hash | ||
| 17 | 7e4f082320b8e9299d4fdb47d84e90282f75441e | SHA1 Hash | Stage 4 dropper.exe – 1 |
| 37af3dd3964b98a4296a266ef4ca71febd61755c9e7a248bc05a5b5ce5be91dc | SHA256 Hash | ||
| ed3dc99329202fa901203b8100643357 | MD5 Hash | ||
| 18 | 7e4f082320b8e9299d4fdb47d84e90282f75441e | SHA1 Hash | Stage 4 dropper.exe – 2 |
| 37af3dd3964b98a4296a266ef4ca71febd61755c9e7a248bc05a5b5ce5be91dc | SHA256 Hash | ||
| ed3dc99329202fa901203b8100643357 | MD5 Hash | ||
| 19 | 947bc0e75649c5dfe3822ba983fcb66f72f97325 | SHA1 Hash | Stage 4 dropper.exe – 3 |
| e3aafbb5792fe5ba59fd33eb696efa4f92937f99f231f0dbf68dcdeeeca0226f | SHA256 Hash | ||
| 318686da42c473d1e1830ef038f80749 | MD5 Hash | ||
| 20 | d25340ae8e92a6d29f599fef426a2bc1b5217299 | SHA1 Hash | WniRing0.sys |
| 11bd2c9f9e2397c9a16e0990e4ed2cf0679498fe0fd418a3dfdac60b5c160ee5 | SHA256 Hash | ||
| 0c0195c48b6b8582fa6f6373032118da | MD5 Hash | ||
| 21 | 1701478a9e499f0545188a84f1eb2d11c7fbd4e5 | SHA1 Hash | Stage 5 XMRrig.exe – 1 |
| 0b73a0a29425663deeecfcf7231ec57c827e2c00bee1cc854f100f544a520fcd | SHA256 Hash | ||
| 801d370ed441d0dc9dc1dd4d26f0a710 | MD5 Hash | ||
| 22 | 89e2843362748e1206cc59946923e15c4450bc82 | SHA1 Hash | Stage 5 XMRrig.exe – 2 |
| b531b2e06b0d3bafabad968f28a255eeb61132dc3eafd76680d16e280790a5fe | SHA256 Hash | ||
| 0282de7d55c591fea67ecb0629bfc78d | MD5 Hash | ||
| 23 | e0d39d79e53a27c32a251b2f4b7476e24f95a80b | SHA1 Hash | Stage 5 XMRrig.exe – 3 |
MITRE ATT&CK TTPs
| Sr. No. | Tactic | Technique |
| 1 | Execution (TA0002) | T1059.001 : Powershell |
| T1059.003 : Windows Command Shell | ||
| 2 | Privilege Escalation (TA0004) | T1068 : Exploitation for privilege escalation |
| T1574.002 : DLL Side Loading | ||
| 3 | Defense Evasion (TA0005) | T1027.009: Embedded Payloads |
| T1055.001 : Dynamic-link Library Injection | ||
| T1055.002 : Portable Executable Injection | ||
| T1140: De-obfuscate/Decode Files or Information | ||
| T1497: Virtualization/Sandbox Evasion | ||
| T1562.001 : Impair Defenses: Disable or Modify Tools | ||
| T1622: Debugger Evasion | ||
| 4 | Command and Control (TA0011) | T1071.001 : Web Protocols |
| 5 | Impact (TA0040) | T1496 : Resource Hijacking |
| 6 | Resource Development (TA0042) | T1608 : Stage Capabilities |
RECOMMENDATIONS
- Deploy robust endpoint security solutions with advanced threat detection and prevention mechanisms to effectively identify and neutralize malicious activities.
- Employ reputable antivirus and anti-malware software capable of promptly detecting and removing malicious payloads to enhance overall system security.
- Ensure regular updates for operating systems, applications, and security software to address known vulnerabilities frequently exploited by threat actors.
- Implement network segmentation to limit lateral movement, preventing malware from accessing critical assets and containing potential threats.
- Configure firewalls to block outbound communication with known malicious IP addresses and domains linked to command-and-control servers.
- Implement behaviour-based monitoring to detect unusual activity patterns, including suspicious processes attempting unauthorized network connections.
- Enforce application whitelisting policies to permit only approved applications, preventing the execution of unauthorized or malicious executables.
- Recognize normal CPU activity and monitor for abnormal activity.
- Monitor network traffic for anomalous patterns, such as large data transfers to unfamiliar or suspicious IP addresses, indicates potential threats.
- Stay informed with the latest threat intelligence reports and indicators of compromise related to malware to proactively identify and mitigate potential threats.
- Build and implement safeguarding measures by monitoring/blocking Indicators of Compromise (IOCs) and enhancing defense based on tactical intelligence and provided rules.

